Authentication
Ayyeka supports the oAuth2 protocol for authorizing access to REST-API. This allows Ayyeka to protect the API so that only allowed users can perform requests to it.
Only the client credentials grant type is supported. For more information about oAuth2.0 click on OAuth 2.0 Authorization Framework.
API Client - Key, Secret
The first thing required by the user is to create an API Client Key, Secret in the FAI platform, you are required to perform this step to avoid using users' usernames and passwords in their API client.
- Go to the platform menu and click on the API menu item.
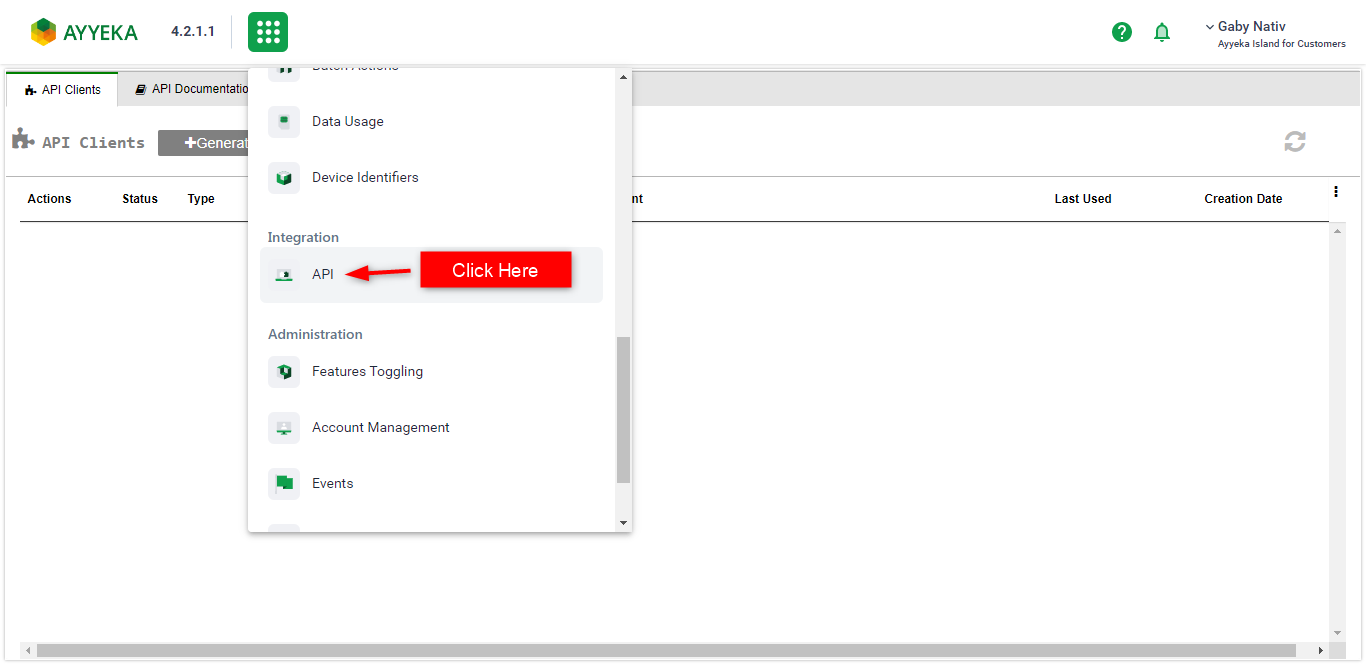
- In the API Clients Tab, define a new API Client by clicking Generate API Key. We recommend writing a comment that describes the purpose of this API client for traceability.
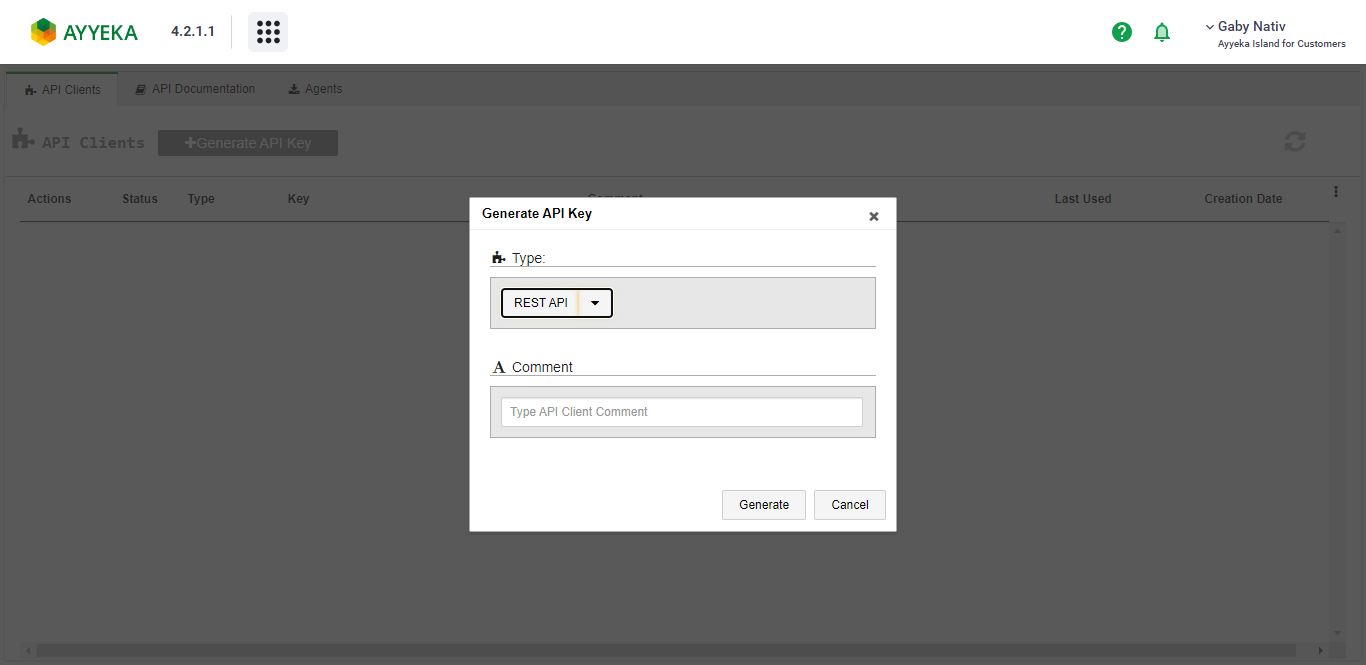
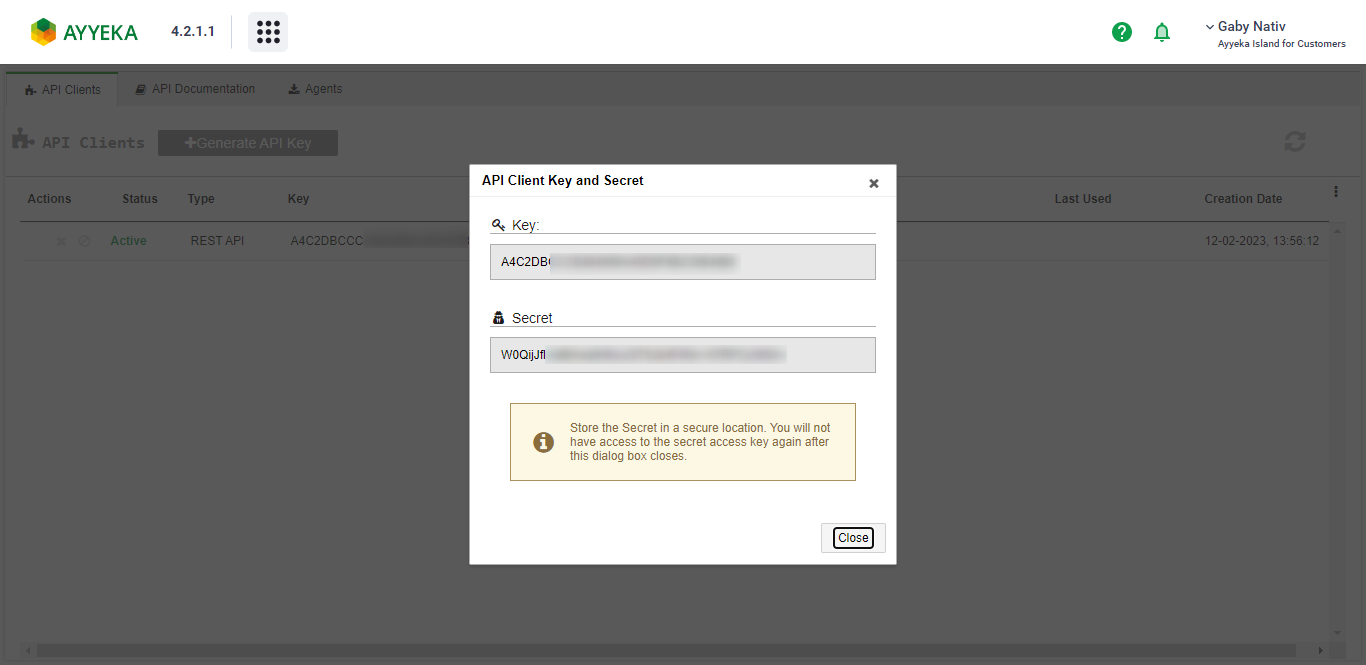
- Use the generated Key and Secret in the next step below.
Getting JWT Access Token
The next step is to call the platform's oAuth2 service to get the access token.
-
Generate an
b64_auth_stringby base64 formatting acquired Key and the Secret with colon punctuation
b64_auth_string = base64 ( Key:Secret) -
Perform a request to an oAuth2 service for an access token, a user must include the Authorization request header with the
auth_stringPOST /auth/token HTTP/1.1 Host: https://restapi.ayyeka.com/auth/token Content-Type: application/x-www-form-urlencoded Authorization: Basic b64_auth_string Cache-Control: no-cache grant_type= client_credentialsHTTP/1.1 200 OK Cache-Control: no-store Content-Type: application/json; charset=utf-8 Date: Mon, 15 Feb 2023 14:36:08 GMT Pragma: no-cache Content-Length: 231 Connection: keep-alive {"access_token":"eyJhbGciOiJSUzM4NCIsInR5cCI6IkpXVCJ9.eyJhdWQiOiIyMDkxIiwiZXhwIjoxNjc2MjE0NTQ2LCJpYXQiOjE2NzYyMTA5NDYsImlzcyI6IkNsb3VkIiwic3ViIjoiNjIzNzo3MDgifQ.SEEDMsh4rmm2EstcjCaUhDScgqQIc-SWZZz7dnPslNNBVtWq_VfNvEQgUo8V3cCt3vr95GRMKkOV5k02VDVymq4xJc3fW-LFwXp0OHNIYM1W2BGETy4wThJqvneYHS6L8NwY2KHd9GVuD8p9VRUaPBZb_7fTotMMO7NwYu7gGfh34d4Zra4GWfml65d3WV-0BzM2pWokC6qtWYowLMon6uKrcXQhWOknGocx1h59ocCK9I0eC2sECgYJ7y1NIIiJmmAZdTqudJDQpBG0PvqjkZaVS4vP4qCQoe0N88iAZ8VVnzJoR5I3TKe8SJfpJPOCVYmJ8H9PhD1d-IFEk1csmBYQudA8-OM-pu7bj0m-5V_C0YdsxmlR_cM_F_bndm2S258eZKMfKrBFtq6NDJACR4CtqScrI3Bb-xlpzo2jItPYY4edIv7hgt9VTFY-HB5IQMstFDihfWGjLIH-2HoXQWpY-He5moHB6B75HtuqKyIo9hEFec1QQ2hkm7AN9uuo","token_type":"JWT","expires_in":3600}the response body is a JSON format, user can use the
expires_infield to understand when the next time is required to request a new access token.{ "access_token": "eyJhbGciOiJSUzM...", "token_type": "JWT", "expires_in": 3600 }
Calling the API
When performing an API request user must include the Authorization request header with the value of the field access_token
GET /v2.0/site HTTP/1.1
Host: <Authentication Server URL>
Authorization:Bearer eyJhbGciOiJSUzM...
Cache-Control: no-cache
Updated 9 months ago
